Urgent Need for Secure Autonomy
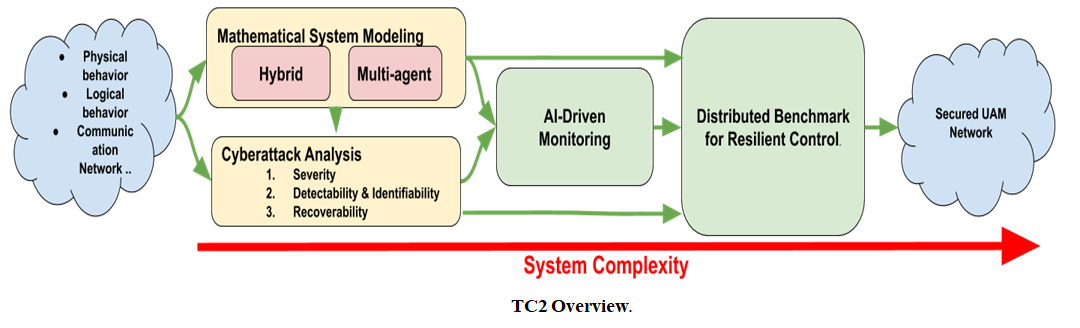
Conventional security techniques alone will not assure future UAM’s security and safety, while traditional fault-tolerant control methods are not directly applicable to achieve resiliency against malicious cyber-physical attacks (e.g., Denial-of-Service, Distributed Denial-of-Service, Man-in-the-Middle (MitM), and Eavesdropping, etc.) with sophisticated spoofs of the monitoring system. Challenges for secured UAM systems come from the inherent heterogeneity of their physical components, the large scale and limited computation/processing capability of their individual components, and the hostile, highly dynamic environment